Former intelligence analyst and whistleblower, Edward Snowden – speaking live to those gathered at the Auckland Town Hall on Monday September 17, 2014. Investigation by Selwyn Manning (updated). THE PRIME MINISTER JOHN KEY’s admission in September 2014 that whistleblower Edward Snowden “may well be right” that our data-communications may be accessible through XKeyscore raises further questions of whether the Prime Minister has told the ‘whole truth’ or whether he is simply out of his depth on global intelligence operations. The New Zealand Herald reported in September 2014:
Prime Minister John Key acknowledged today that NSA whistleblower Edward Snowden’s claim that New Zealanders’ data is accessible through the controversial XKeyscore system “may well be right”.However, the Prime Minister then maintained that information will not have been gathered under any Government Communications Security Bureau (GCSB) mass surveillance programme as the agency doesn’t have that capability. (Ref. NZHerald). That statement is clearly polls apart from the revelations published in a cooperative effort by investigative journalist Nicky Hager, the New Zealand Herald’s David Fisher, and the Sunday Star Times (pending publication). The contradictory statements raise questions as to whether the Prime Minister has been outplayed by the deep state, the true masters of the great game? If not, then it suggests John Key is attempting to prevent New Zealanders from knowing what his government is permitting in our name. Whatever the truth is, the issue drives home the need for New Zealanders to fast become familiar with what the United States-based spy agency does, its reach around the world, how it sets up sites in countries like ours, and importantly what the National Security Agency (NSA), has already admitted to. Is New Zealand merely a pawn in a US-led system designed to protect the superpower’s economic and foreign policy interests? The Snowden Revelations suggest this is so. Has the NSA a facility in New Zealand as whistleblower Edward Snowden suggests? To consider this we need to realise that the agency has many difference faces. Let’s consider: how does the NSA operate? How does it use privately owned businesses, corporations, to do its work abroad? How does it partner up with such players to construct what is simply a spy network of privately owner profitable cells and government agencies all feeding back to the mothership Stateside? Is this the ultimate version of a public-private-partnership (PPP)? And, is this how it masks, in part, its operation around the globe?
 Companies like Palantir International, conceived deep within California’s Silicon Valley, has become a giant among the technology companies that have made millions and millions of dollars networking with governments and the world’s largest spy agencies – the Central Intelligence Agency (CIA) and the NSA among them.
Palantir Technologies New Zealand Ltd is operating in New Zealand. Now, we do not at this juncture suggest Palantir is operating in New Zealand at the behest of the NSA, but we can confirm that it registered as a company here in 2012, its official office is listed in the Government companies office register as being with legal firm Simpson Grierson, 88 Shortland St, Auckland; that it has a headquarters in Wellington; it recruited for interns at Victoria University as recently as May 19 this year; it actively employed data analysis and computer engineers at locations in New Zealand, has invested around $12 million into New Zealand information communication technology (ICT) start-ups, and certainly specialises in highly efficient deep data analysis on a global-scale.
Palantir states on the New Zealand section of its global corporate website: “We are composed of technical people doing technical work, software engineers who establish natural rapport before discussing solutions and pounding the keyboard, analysts who can tweak servers, and communicators who listen. Our goal is to implement our platform where people need it, without a surplus of jargon. We don’t do business as usual; we do business as Palantir.”
So what is this business it speaks of?
Well the Wall Street Journal describes one of its products, Palantir Gotham, as: Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community and United States Department of Defense, fraud investigators at the Recovery Accountability and Transparency Board, and cyber analysts at Information Warfare Monitor (responsible for the GhostNet [a Chinese cyber attack network] and the Shadow Network investigation). Palantir Metropolis is used by hedge funds, banks, and financial services firms. (Ref. WSJ).
WSJ wrote in the early stages of Palantir’s rise:
Companies like Palantir International, conceived deep within California’s Silicon Valley, has become a giant among the technology companies that have made millions and millions of dollars networking with governments and the world’s largest spy agencies – the Central Intelligence Agency (CIA) and the NSA among them.
Palantir Technologies New Zealand Ltd is operating in New Zealand. Now, we do not at this juncture suggest Palantir is operating in New Zealand at the behest of the NSA, but we can confirm that it registered as a company here in 2012, its official office is listed in the Government companies office register as being with legal firm Simpson Grierson, 88 Shortland St, Auckland; that it has a headquarters in Wellington; it recruited for interns at Victoria University as recently as May 19 this year; it actively employed data analysis and computer engineers at locations in New Zealand, has invested around $12 million into New Zealand information communication technology (ICT) start-ups, and certainly specialises in highly efficient deep data analysis on a global-scale.
Palantir states on the New Zealand section of its global corporate website: “We are composed of technical people doing technical work, software engineers who establish natural rapport before discussing solutions and pounding the keyboard, analysts who can tweak servers, and communicators who listen. Our goal is to implement our platform where people need it, without a surplus of jargon. We don’t do business as usual; we do business as Palantir.”
So what is this business it speaks of?
Well the Wall Street Journal describes one of its products, Palantir Gotham, as: Palantir Gotham is used by counter-terrorism analysts at offices in the United States Intelligence Community and United States Department of Defense, fraud investigators at the Recovery Accountability and Transparency Board, and cyber analysts at Information Warfare Monitor (responsible for the GhostNet [a Chinese cyber attack network] and the Shadow Network investigation). Palantir Metropolis is used by hedge funds, banks, and financial services firms. (Ref. WSJ).
WSJ wrote in the early stages of Palantir’s rise:
Palantir’s software has helped root out terrorist financing networks, revealed new trends in roadside bomb attacks, and uncovered details of Syrian suicide bombing networks in Iraq, according to current and former U.S. officials familiar with the events. It has also foiled a Pakistani suicide bombing plot on Western targets and discovered a spy infiltration of an allied government. It is now being used by the Central Intelligence Agency, the Pentagon and the Federal Bureau of Investigation. Yet Palantir — which takes its name from the “seeing stones” in the “Lord of the Rings” series — remains an outlier among government security contractors.Only yesterday (September 15, 2014 US timezone) Palantir was cited in the Silicon Valley Business Journal as adding US$50 million to its corporate spy war-chest. Palantir Technologies disclosed on Friday that it has raised $50 million more in a funding round that now totals about $444 million. The secretive Palo Alto Big Data analytics company led by Alex Karp didn’t disclose where the funding came from in its filing with the Securities and Exchange Commission. The company was already one of the most heavily funded startups in Silicon Valley. It raised a total of $829 million before this latest funding. (Ref. SVBJ). The report noted: Palantir’s backers include the CIA’s In-Q-Tel venture fund and, the company’s co-founder Peter Thiel’s Founders Fund. The report listed among its customer’s the US “government intelligence agencies such as the National Security Agency”. All of this material is easily accessed via the internet. It would be helpful if New Zealand’s Prime Minister John Key revealed what exactly Palantir Technologies New Zealand Ltd is doing here, particularly as the company states in its recruitment material that it is working with government to deploy its platform. What platform is this? Why is this company so intent on establishing itself here? It would also be worthwhile for all those interested in investigating Edward Snowden’s claim – that the NSA has operations in at least two locations, one in Auckland (perhaps located near the Southern Cross cable underground hub on Auckland’s North Shore, that feeds large capacity to the Albany IT sector) and another north of the city – to consider the PPP tactic. Companies like Palantir have the expertise and the track-record of getting results for their clients For example, Palantir’s corporate website states: “DATA FUSION PLATFORMS Back-end infrastructure for integrating, managing, and securing data of any kind, from any source, at massive scale.” (Ref. Palantir.com). In 2012, shortly after it established in New Zealand, Palantir was actively recruiting for IT specialists. For example:
Palantir is looking for a brilliant, technical mind to help deploy our Government platform in New Zealand. We need someone to take a step back, look at who we are interacting with, and what those interactions mean across the organisation.It offered insight into what it does, stating: We currently offer a suite of software applications for integrating, visualizing and analyzing the world’s information. We support many kinds of data including structured, unstructured, relational, temporal and geospatial. (Ref. LinkedIn). Describing its operation, Palantir wrote it is: “broadly deployed in the intelligence, defense, law enforcement and financial communities, and are spreading rapidly by word of mouth into applications in other industries and realms of impact.” Palantir clearly has an overt presence here in New Zealand. And nothing suggests its operation is anything other than lawful. The above references are cited in the public interest simply to illustrate how state spy agencies contract and outsource to the private/corporate sector, and how the private/corporate sector accumulates vast profits in what is a very lucrative field.
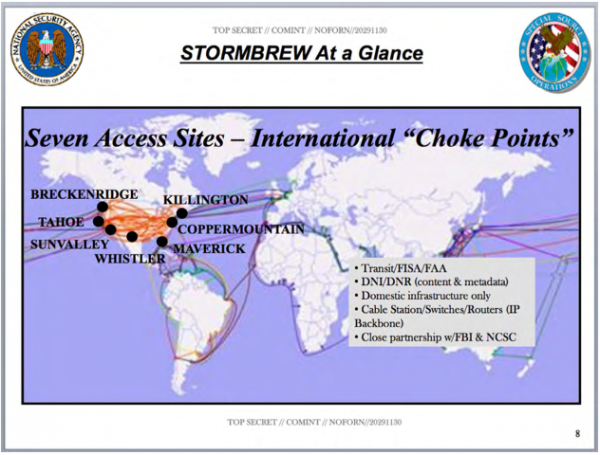 StormBrew.[/caption]
STORMBREW: Location, Auckland, NZ. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 107).
StormBrew.[/caption]
STORMBREW: Location, Auckland, NZ. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 107).
-
The jargon: DNI/DNR = CONTENT AND METADATA; DOMESTIC INFRASTRUCTURE ONLY; CABLE STATION/SWITCHES/ROUTERS/IP BACKBONE); CLOSE PARTNERSHIP WITH FBI & NCSC.
-
DNI Selectors = 9 US based service providers (PRISM). Worldwide sources (UPSTREAM).
DNR Selectors = Worldwide sources.
 The pre-positioning access-points into hard-target networks worldwide. (Ref. NoPlaceToHide Greenwald/Snowden doc: Slide, Page 149).[/caption]
WHAT’S ALL THIS ABOUT METADATA THEN?
Metadata is the tip of the surveillance iceberg. As Edward Snowden said on Monday night, metadata is an analyst’s dream as it doesn’t lie. It shows who a person talked to, the time, the location, the duration. It can easily be cross referenced and applied layer upon layer. It can be visually analysed, geospatial analysis can be used to identify patterns of connections between disparate groups, cells, networks, individuals. This data is powerful.
Back to Xkeyscore.
XKeyScore acquires your information via DNI Upstream sensor sites (which Snowden referred to as being located in Auckland and Northland) and pre-positioned access points at ISPs (a capability that the GCSB and TICS legislation made lawful and asserted a requirement obligation on the country’s ISPs).
The principle of mass surveillance is a matter of definition. What governments define as surveillance is often quite different to how you or I may define the word.
But for the purpose of this piece, surveillance – whether it be technology-driven dragnet ‘indiscriminate’ surveillance, or human analyst driven search surveillance – it is one of the same. It involves four elements: Trafficthief (metadata), Pinwale, MARINA, and the big foundation of the four: XKeyScore.
[caption id="attachment_52532" align="alignleft" width="565"]
The pre-positioning access-points into hard-target networks worldwide. (Ref. NoPlaceToHide Greenwald/Snowden doc: Slide, Page 149).[/caption]
WHAT’S ALL THIS ABOUT METADATA THEN?
Metadata is the tip of the surveillance iceberg. As Edward Snowden said on Monday night, metadata is an analyst’s dream as it doesn’t lie. It shows who a person talked to, the time, the location, the duration. It can easily be cross referenced and applied layer upon layer. It can be visually analysed, geospatial analysis can be used to identify patterns of connections between disparate groups, cells, networks, individuals. This data is powerful.
Back to Xkeyscore.
XKeyScore acquires your information via DNI Upstream sensor sites (which Snowden referred to as being located in Auckland and Northland) and pre-positioned access points at ISPs (a capability that the GCSB and TICS legislation made lawful and asserted a requirement obligation on the country’s ISPs).
The principle of mass surveillance is a matter of definition. What governments define as surveillance is often quite different to how you or I may define the word.
But for the purpose of this piece, surveillance – whether it be technology-driven dragnet ‘indiscriminate’ surveillance, or human analyst driven search surveillance – it is one of the same. It involves four elements: Trafficthief (metadata), Pinwale, MARINA, and the big foundation of the four: XKeyScore.
[caption id="attachment_52532" align="alignleft" width="565"]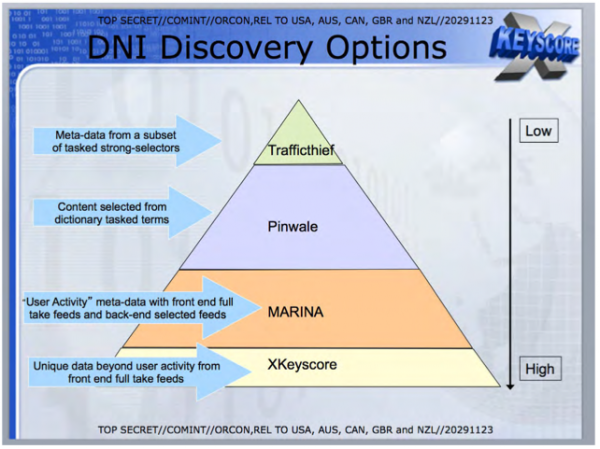 DNI Discovery Options. (Ref. NoPlaceToHide Greenwald/Snowden doc: slide – DNI Discovery Options Page 160).[/caption]
Remember too that with the help of Microsoft, the NSA stated in the source documents that it can easily crack high encryption. It also is able to decipher voice over internet protocol (VOIP) data calls on Skype (something that initially proved tricky).
THE INTERACTION BETWEEN GOVERNMENT BODIES:
Another important aspect to realise is how the NSA shares, cooperates, and utilizes the multiple jurisdictions permitted within separate departments of government.
Crossover and sharing of information is one thing, but sharing capability is the foundation of the relationship between intelligence agencies and the major estates of government.
We realised this to a degree in 2013 when it became known that the New Zealand GCSB was acting unlawfully when assisting the New Zealand Police to surveil Kim Dotcom. It also came to pass that 88 other New Zealand citizens or residents had also been unlawfully surveilled, although the circumstances of those offences were never revealed.
Let’s consider SIGINT (or signals intelligence). SIGINT developed as a primary tool of defence and military when acquiring intelligence on an enemy. But the NSA documents reveal SIGINT is vital to its ‘indiscriminate’ surveillance operations against the citizenry. Here in New Zealand, until recent times, the GCSB’s primary skill was signals-based.
The relationship between defence SIGINT activity and the NSA’s surveillance of the world’s citizens may also give some clarity as to whether the NSA does have a sensor site in Auckland and Northland. New Zealand Defence facilities are located here. And New Zealand Defence has an intelligence unit intelligence
THE SIGINT DEFENCE CRYPTOLOGIC PLATFORM:
[caption id="attachment_52533" align="alignleft" width="565"]
DNI Discovery Options. (Ref. NoPlaceToHide Greenwald/Snowden doc: slide – DNI Discovery Options Page 160).[/caption]
Remember too that with the help of Microsoft, the NSA stated in the source documents that it can easily crack high encryption. It also is able to decipher voice over internet protocol (VOIP) data calls on Skype (something that initially proved tricky).
THE INTERACTION BETWEEN GOVERNMENT BODIES:
Another important aspect to realise is how the NSA shares, cooperates, and utilizes the multiple jurisdictions permitted within separate departments of government.
Crossover and sharing of information is one thing, but sharing capability is the foundation of the relationship between intelligence agencies and the major estates of government.
We realised this to a degree in 2013 when it became known that the New Zealand GCSB was acting unlawfully when assisting the New Zealand Police to surveil Kim Dotcom. It also came to pass that 88 other New Zealand citizens or residents had also been unlawfully surveilled, although the circumstances of those offences were never revealed.
Let’s consider SIGINT (or signals intelligence). SIGINT developed as a primary tool of defence and military when acquiring intelligence on an enemy. But the NSA documents reveal SIGINT is vital to its ‘indiscriminate’ surveillance operations against the citizenry. Here in New Zealand, until recent times, the GCSB’s primary skill was signals-based.
The relationship between defence SIGINT activity and the NSA’s surveillance of the world’s citizens may also give some clarity as to whether the NSA does have a sensor site in Auckland and Northland. New Zealand Defence facilities are located here. And New Zealand Defence has an intelligence unit intelligence
THE SIGINT DEFENCE CRYPTOLOGIC PLATFORM:
[caption id="attachment_52533" align="alignleft" width="565"]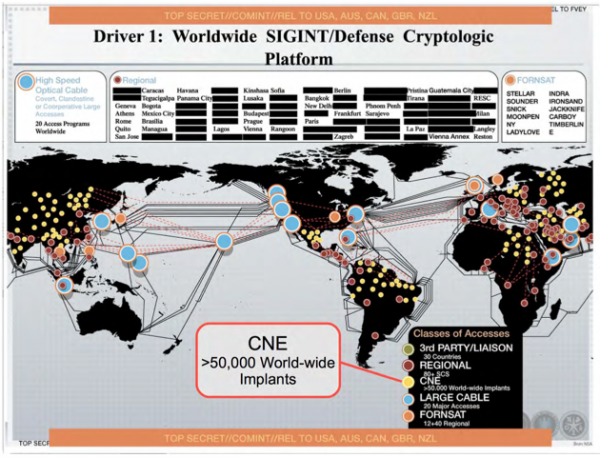 SIGINT-defence Cryptologic Platform. (Ref. CNE access at 50,000 locations worldwide including Auckland, New Zealand. Ref. NoPlaceToHide Greenwald/Snowden doc: Page 117).[/caption]
We know from the NSA’s own documents that the National Security Agency/Central Security Service shares “technological developments, cryptologic capabilities, software and resources for state-of-the-art collection, processing and analytical efforts, and IA capabilities.”
The intelligence exchange with Canada for example “covers national and transnational targets. No Consolidated Cryptologic Program (CCP) money is allocated to CSEC (Canada’s Communications Security Establishment Canada), but NSA at times pays R&D and technology costs on shared projects with CSEC.”
It has long been a question that remains unanswered as to whether New Zealand has received money to assist its spying for the Five Eyes Intelligence Agency. The Canadian experience suggests that at least in part, New Zealand has.
Some may ask, why would sovereign states like New Zealand, with a history of independent foreign policy give so much control away to a foreign superpower?
So what does the Five Eyes Intelligence Agency offer? Well, the NSA states the answer as: “… resources for advanced collection, processing and analysis” and open sharing of information/intelligence gathered via “covert sites at the request of NSA”.
In return, the Five Eyes member states provide the NSA “unique geographic access to areas unavailable to the U.S.”. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 121).
The NSA documents also state “comprehensive cooperation” is provided to ‘first tier’ member states Australia, Canada, New Zealand and the United Kingdom. While “focused cooperation” is exchanged with Austria, Belgium, Czech Republic, Denmark, Germany, Greece, Hungary and 13 other nations.
GEOGRAPHICAL REGIONAL SIGNIFICANCE:
SIGINT-defence Cryptologic Platform. (Ref. CNE access at 50,000 locations worldwide including Auckland, New Zealand. Ref. NoPlaceToHide Greenwald/Snowden doc: Page 117).[/caption]
We know from the NSA’s own documents that the National Security Agency/Central Security Service shares “technological developments, cryptologic capabilities, software and resources for state-of-the-art collection, processing and analytical efforts, and IA capabilities.”
The intelligence exchange with Canada for example “covers national and transnational targets. No Consolidated Cryptologic Program (CCP) money is allocated to CSEC (Canada’s Communications Security Establishment Canada), but NSA at times pays R&D and technology costs on shared projects with CSEC.”
It has long been a question that remains unanswered as to whether New Zealand has received money to assist its spying for the Five Eyes Intelligence Agency. The Canadian experience suggests that at least in part, New Zealand has.
Some may ask, why would sovereign states like New Zealand, with a history of independent foreign policy give so much control away to a foreign superpower?
So what does the Five Eyes Intelligence Agency offer? Well, the NSA states the answer as: “… resources for advanced collection, processing and analysis” and open sharing of information/intelligence gathered via “covert sites at the request of NSA”.
In return, the Five Eyes member states provide the NSA “unique geographic access to areas unavailable to the U.S.”. (Ref. NoPlaceToHide Greenwald/Snowden doc: Page 121).
The NSA documents also state “comprehensive cooperation” is provided to ‘first tier’ member states Australia, Canada, New Zealand and the United Kingdom. While “focused cooperation” is exchanged with Austria, Belgium, Czech Republic, Denmark, Germany, Greece, Hungary and 13 other nations.
GEOGRAPHICAL REGIONAL SIGNIFICANCE:
 While the United States is able to reach and breach information on a global scale, its partners of the Five Eyes Intelligence Agency are valuable in part due to their location and geopolitical idiosyncrasies. Each has a unique opportunity capability.
The NSA documents show that Australia’s location and interactivity with Indonesia assists the NSA to target “high priority targets” inside Indonesia.
While it is yet to be clear what New Zealand provides the NSA in terms of international trading partner intelligence, New Zealand’s relationship and trading status with the People’s Republic of China provides a specific and unique trade-led environment that others, including the USA, do not share.
Also, New Zealand’s capital city Wellington is the location of a significant French diplo-contingent. The French Embassy in Wellington is the fourth largest of France’s foreign affairs posts and interconnects with France’s territories in Polynesia and French Polynesia. This includes its need to assist in the transit of its military hardware in the wider Pacific basin.
New Zealand’s external offshore signals surveillance, via the GCSB base at Waihopai, is now well known. What is not so well appreciated is that the GCSB’s patch is east of Australia’s east coast, northward and eastward then out into Polynesia and French Polynesia. It would seem likely that China aside, France’s interests in the Pacific are the target of New Zealand Government spying.
While the United States is able to reach and breach information on a global scale, its partners of the Five Eyes Intelligence Agency are valuable in part due to their location and geopolitical idiosyncrasies. Each has a unique opportunity capability.
The NSA documents show that Australia’s location and interactivity with Indonesia assists the NSA to target “high priority targets” inside Indonesia.
While it is yet to be clear what New Zealand provides the NSA in terms of international trading partner intelligence, New Zealand’s relationship and trading status with the People’s Republic of China provides a specific and unique trade-led environment that others, including the USA, do not share.
Also, New Zealand’s capital city Wellington is the location of a significant French diplo-contingent. The French Embassy in Wellington is the fourth largest of France’s foreign affairs posts and interconnects with France’s territories in Polynesia and French Polynesia. This includes its need to assist in the transit of its military hardware in the wider Pacific basin.
New Zealand’s external offshore signals surveillance, via the GCSB base at Waihopai, is now well known. What is not so well appreciated is that the GCSB’s patch is east of Australia’s east coast, northward and eastward then out into Polynesia and French Polynesia. It would seem likely that China aside, France’s interests in the Pacific are the target of New Zealand Government spying.
 SO WHAT HAPPENS TO ALL THIS INFORMATION?
So where does this intelligence all end up?
What kind of personal information is gathered?
The NSA documents show us that virtually everything is acquired.
Internet surfing, webmail (Yahoo, Hotmail, Gmail etc), Facebook, Myspace etc, internet searching (Google, Bing, Wikipedia etc), online mapping (Google Maps, Mapquest etc).
Xkeyscore and a number of other platforms collect all forms of communications. To cite the NSA: “Communications, day to day activities, contacts and social networks, photographs, videos, personal information (e.g. addresses, phone, email addresses), location and travel information.”
Facebook, Myspace, Bebo, and now Kik, Instagram, Twitter and a host of other social media platforms provide the NSA “A very rich source of information on targets: personal details, pattern of life, connections and associates, media,” the NSA documents state.
And social media friends… if you think Facebook’s lockdown security settings provide you with privacy, think again. The NSA’s ‘Passive’ system enables this global system: “the opportunity to collect this information by exploiting inherent weaknesses in Facebook’s security model.”
[caption id="attachment_52536" align="alignleft" width="565"]
SO WHAT HAPPENS TO ALL THIS INFORMATION?
So where does this intelligence all end up?
What kind of personal information is gathered?
The NSA documents show us that virtually everything is acquired.
Internet surfing, webmail (Yahoo, Hotmail, Gmail etc), Facebook, Myspace etc, internet searching (Google, Bing, Wikipedia etc), online mapping (Google Maps, Mapquest etc).
Xkeyscore and a number of other platforms collect all forms of communications. To cite the NSA: “Communications, day to day activities, contacts and social networks, photographs, videos, personal information (e.g. addresses, phone, email addresses), location and travel information.”
Facebook, Myspace, Bebo, and now Kik, Instagram, Twitter and a host of other social media platforms provide the NSA “A very rich source of information on targets: personal details, pattern of life, connections and associates, media,” the NSA documents state.
And social media friends… if you think Facebook’s lockdown security settings provide you with privacy, think again. The NSA’s ‘Passive’ system enables this global system: “the opportunity to collect this information by exploiting inherent weaknesses in Facebook’s security model.”
[caption id="attachment_52536" align="alignleft" width="565"]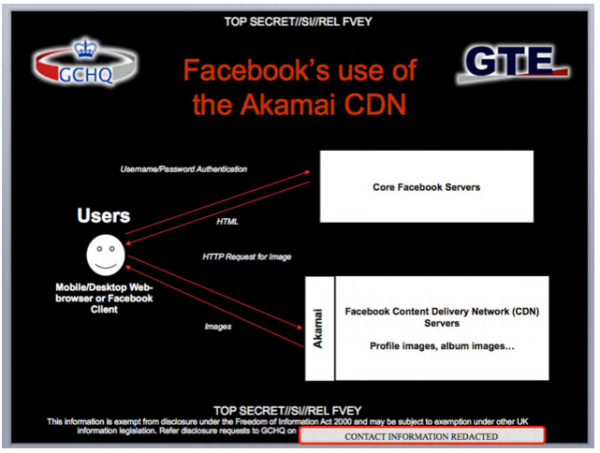 Facebook Surveillance.[/caption]
Also, at the time the NSA documents were acquired, the Five Eyes alliance was advancing its capability to track and monitor communications passengers of aircraft.
The UK’s GCHQ was leading this breakthrough technology. This new system referred to as Thieving Magpie hacks into any GSM and GPRS calls and data communications emitting form onboard aircraft. It is able to probe such communications every two seconds, while the aircraft is flying anywhere in the world.
In 2013 the NSA documents noted that “many airlines are offering on-board mobile phone services, particularly for long haul and business class (list is growing).”
Thieving Magpie was anticipated to provide XKeyScore “global coverage” via its Southwinds platform at some stage in 2014.
This technology announcement was provided to all Five Eyes member agencies, including New Zealand’s GCSB.
Of course, the New Zealand National-led Government has not informed its citizenry of any of this information.
The GCSB was informed that once Thieving Magpie’s global capability is achieved it will be “available to FVEY (Five Eyes) users” via a simple to use “light weight web page”.
THE SINISTER SIDE OF OUR SPYS’ METHODS:
Facebook Surveillance.[/caption]
Also, at the time the NSA documents were acquired, the Five Eyes alliance was advancing its capability to track and monitor communications passengers of aircraft.
The UK’s GCHQ was leading this breakthrough technology. This new system referred to as Thieving Magpie hacks into any GSM and GPRS calls and data communications emitting form onboard aircraft. It is able to probe such communications every two seconds, while the aircraft is flying anywhere in the world.
In 2013 the NSA documents noted that “many airlines are offering on-board mobile phone services, particularly for long haul and business class (list is growing).”
Thieving Magpie was anticipated to provide XKeyScore “global coverage” via its Southwinds platform at some stage in 2014.
This technology announcement was provided to all Five Eyes member agencies, including New Zealand’s GCSB.
Of course, the New Zealand National-led Government has not informed its citizenry of any of this information.
The GCSB was informed that once Thieving Magpie’s global capability is achieved it will be “available to FVEY (Five Eyes) users” via a simple to use “light weight web page”.
THE SINISTER SIDE OF OUR SPYS’ METHODS:
 Disturbingly, the NSA documents indicate how the use of sinister manipulation can destroy the reputations of Five Eyes targets, the NSA documents also describe how “radicalizers appear to be particularly vulnerable in the area of authority when their private and public behaviors are not consistent.
It lists four behaviors to look out for when surveilling a target, to identify the:
Disturbingly, the NSA documents indicate how the use of sinister manipulation can destroy the reputations of Five Eyes targets, the NSA documents also describe how “radicalizers appear to be particularly vulnerable in the area of authority when their private and public behaviors are not consistent.
It lists four behaviors to look out for when surveilling a target, to identify the:
- “Viewing sexually explicit material online or using sexually explicit persuasive language when communicating with inexperienced young girls;
- Using a portion of the donations they are receiving from the susceptible pool to defray their own personal expenses;
- Charging an exorbitant amount of money for their speaking fees and being singularly attracted by opportunities to increase their status; or
- Being know to base their public messaging on questionable sources or using language that is contradictory in nature, leaving them open to credibility challenges.”
- “Set up a honey-trap
- Change their photos on social networking sites
- Write a blog purporting to be one of their victims
- Email/text their colleagues, neighbors, friends etc.”
 Effects-Definition.[/caption]
This information was presented by the NSA to New Zealand’s GCSB officers are a training/briefing session.
The NSA officer briefing the Five Eyes spies added: “Honey-trap; a great option. Very successful when it works. Get someone to go somewhere on the internet, or a physical location to be met by a ‘friendly face’. JTRIG has the ability to ‘shape’ the environment on occasions.”
The officer adds that changing a person’s photograph on a social media profile page is effective in driving up paranoia: “Can take paranoia to a whole new level.”
And the officer suggests email and txt operations can assist the state’s spies to gain credibility with online groups and infiltration of the same.
The above methods will no doubt ‘ring a few bells’ and cause some unease for New Zealanders who have become privy to the inner workings of Dirty Politics, as practiced by members of the National Party and their attack merchants in the blogosphere and media.
And in case the connection still seems value, here is a direct quote from the NSA briefing to the New Zealand GCSB: “Issues of trust and reputation are important when considering the validity and appeal of the message. It stands to reason that exploiting vulnerabilities of character, credibility, or both, of the radicalizer and his message could be enhanced by an understanding of the vehicles he uses to disseminate his message to the susceptible pool of people and where he is vulnerable in terms of access.”
If the messenger or target ‘radicalizer’ needs to be shut down, the NSA advice is to “Bombard their phone with text messages, bombard their phone with calls, delete their online presence, block up their fax machine.”
If a computer or site or network needs to be taken down, the officer also said: “Send them a virus: Ambassadors reception – encrypt itself, delete all emails, encrypt all files, make the screen shake, no more log on. Conduct a denial of service attack on their computer…”
According to the NSA documents, ‘Effects Operations’ save time and money when compared to “traditional law enforcement”.
And in a section titled: DISRUPTION Operational Playbook, it breaks it down into easy-to-follow terminology:
Effects-Definition.[/caption]
This information was presented by the NSA to New Zealand’s GCSB officers are a training/briefing session.
The NSA officer briefing the Five Eyes spies added: “Honey-trap; a great option. Very successful when it works. Get someone to go somewhere on the internet, or a physical location to be met by a ‘friendly face’. JTRIG has the ability to ‘shape’ the environment on occasions.”
The officer adds that changing a person’s photograph on a social media profile page is effective in driving up paranoia: “Can take paranoia to a whole new level.”
And the officer suggests email and txt operations can assist the state’s spies to gain credibility with online groups and infiltration of the same.
The above methods will no doubt ‘ring a few bells’ and cause some unease for New Zealanders who have become privy to the inner workings of Dirty Politics, as practiced by members of the National Party and their attack merchants in the blogosphere and media.
And in case the connection still seems value, here is a direct quote from the NSA briefing to the New Zealand GCSB: “Issues of trust and reputation are important when considering the validity and appeal of the message. It stands to reason that exploiting vulnerabilities of character, credibility, or both, of the radicalizer and his message could be enhanced by an understanding of the vehicles he uses to disseminate his message to the susceptible pool of people and where he is vulnerable in terms of access.”
If the messenger or target ‘radicalizer’ needs to be shut down, the NSA advice is to “Bombard their phone with text messages, bombard their phone with calls, delete their online presence, block up their fax machine.”
If a computer or site or network needs to be taken down, the officer also said: “Send them a virus: Ambassadors reception – encrypt itself, delete all emails, encrypt all files, make the screen shake, no more log on. Conduct a denial of service attack on their computer…”
According to the NSA documents, ‘Effects Operations’ save time and money when compared to “traditional law enforcement”.
And in a section titled: DISRUPTION Operational Playbook, it breaks it down into easy-to-follow terminology:
- Infiltration Operation<
- Ruse Operation
- Set Piece Operation
- False Flag Operation
- False Rescue Operation
- Disruption Operation
- Sting Operation.